Table Of Contents, Chapter 2
2-1. Computer Network
A computer network is a set of computers sharing resources located on or provided by network nodes. Computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies.
The nodes of a computer network can include personal computers, servers, networking hardware, or other specialized or general-purpose hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol.
Computer networks support many applications and services, such as access to the World Wide Web, digital video and audio, shared use of application and storage servers, printers and fax machines, and use of email and instant messaging applications.
When we get online and connect to internet using a modem or cellular network, just like our home, we would get assigned with an identification such as an address, isp name and our location. So by getting online, we take a place in online world and we communicate with other online participants based on the identifications that we have.
2-2. Internet Protocol (IP)
The address that we get assigned with as soon as we get online, is called an IP address. In todays world, there are 2 types of IP address. Internet Protocol Version 4 (IPv4) and Internet Protocol Version 6 (IPv6). Both of them can be assigned to a client simultaneously. But they are not compatible. IPv4 cannot communicate with IPv6 and vice versa.
The Internet Protocol (IP) is the method for sending data from one device to another across the internet. Every device has an IP address that uniquely identifies it and enables it to communicate with and exchange data with other devices connected to the internet. Today, it’s considered the standard for fast and secure communication directly between mobile devices.
IP is responsible for defining how applications and devices exchange packets of data with each other. It is the principal communications protocol responsible for the formats and rules for exchanging data and messages between computers on a single network or several internet-connected networks. It does this through the Internet Protocol Suite (TCP/IP), a group of communications protocols that are split into four abstraction layers.
IPv4:
IPv4 addresses are 32-bit numbers that are typically displayed in dotted decimal notation. A 32-bit address contains two primary parts: the network prefix and the host number.
All hosts within a single network share the same network address. Each host also has an address that uniquely identifies it. Depending on the scope of the network and the type of device, the address is either globally or locally unique. Devices that are visible to users outside the network (webservers, for example) must have a globally unique IP address. Devices that are visible only within the network must have locally unique IP addresses.
IP addresses are assigned by a central numbering authority that is called the Internet Assigned Numbers Authority (IANA). IANA ensures that addresses are globally unique where needed and has a large address space reserved for use by devices not visible outside their own networks.
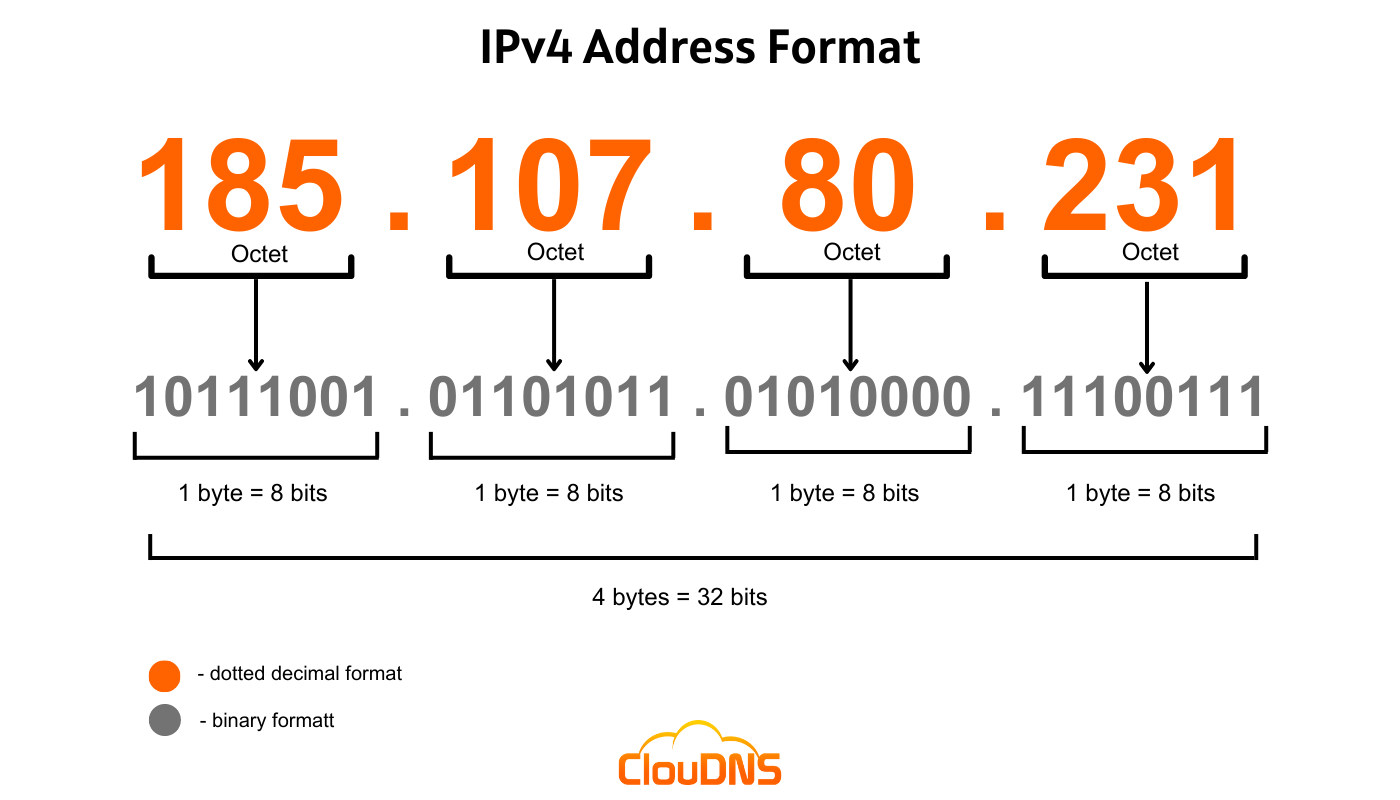 an example of IPv4 structure.
an example of IPv4 structure.
IPv4 Address Structure
An IPv4 address is 32 bits long and is typically written in dotted decimal notation, consisting of four-octets (8-bit segments) separated by periods. For example: 192.168.0.1.
Address Classes
Class A
- Range: 1.0.0.0 to 126.0.0.0
- Leading Bits: 0
- Default Subnet Mask: 255.0.0.0 (/8)
- Number of Networks: 128 (2^7, minus reserved addresses)
- Number of Hosts per Network: 16,777,214 (2^24 - 2, because the first address is the network address and the last is the broadcast address)
- Usage: Designed for very large networks. Rarely used today due to the inefficiency of address space allocation.
Class B
- Range: 128.0.0.0 to 191.255.0.0
- Leading Bits: 10
- Default Subnet Mask: 255.255.0.0 (/16)
- Number of Networks: 16,384 (2^14)
- Number of Hosts per Network: 65,534 (2^16 - 2)
- Usage: Designed for medium-sized networks, such as universities and large businesses.
Class C
- Range: 192.0.0.0 to 223.255.255.0
- Leading Bits: 110
- Default Subnet Mask: 255.255.255.0 (/24)
- Number of Networks: 2,097,152 (2^21)
- Number of Hosts per Network: 254 (2^8 - 2)
- Usage: Designed for small networks, commonly used in small to mid-sized businesses.
Class D
- Range: 224.0.0.0 to 239.255.255.255
- Leading Bits: 1110
- Default Subnet Mask: Not applicable (used for multicast)
- Usage: Reserved for multicast groups, used to send data to multiple destinations simultaneously.
Class E
- Range: 240.0.0.0 to 255.255.255.255
- Leading Bits: 1111
- Default Subnet Mask: Not applicable (reserved for experimental use)
- Usage: Reserved for experimental purposes and not used in public networks.
Example Address and Class Identification
Let's look at an example IPv4 address: "172.16.254.1".
- Determine the first octet: 172
- Identify the class:
- 172 falls within the range 128 to 191, which corresponds to Class B.
- Default subnet mask: For Class B, the default subnet mask is 255.255.0.0 (/16).
Subnet Masks
Let's we are starting an small datacenter. We need to buy IP ranges. For example, we directly request from IANA (which it's not possible nowadays because I believe they've sold out their IPv4. They may be generous with IPv6) and they give us an IPv4 range of 167.235.73.0/24. The /24 subnet mask means that first 3 octets (2^24) which are the networks, are static and you only have 256 hosts on your last octet (32-24=8, 2^8=256). Which 254 are usable due to one of them being a network address and other one being the broadcast address. It's obvious that /16 and /8 subnets are more expensive since they give you more hosts.
IPv6 is the more recent protocol which got implemented due to the shortage of IPv4. Unlike IPv4, they are 128-bits and are quite large. IPv6 addresses are out of scope of this tutorial.
2-3. Word Wide Web (www)
It has happened for you to use a modem as your home network. Or wireless modems such as TD-LTE or Point-to-point. On every single one of them (even your mobile carrier network), as soon as you get online, you get assigned with an IP address. As explained on the past section, an IP address defines your online identity. And with that IP address, you can communicate with other online devices with their own unique IP address. So a public IP address is unique and can't be assigned multiple times. But what happens when multiple devices connect to a single modem? Do they get different IP addresses each? The answer is yes and no! Let's break this down.
I used the term "Public IP address" when I said a device gets online. But let's say we are getting connected to a modem (or a router, or a portable wifi hotspot, etc). Each of the devices that are connected to the modem, share the same public IP address. So whatever the modems public IP address is, we get that on each of the devices connected to the modem. On the other hand, each of the connected devices have a unique local IP address. local IP ranges cannot be public. we mentioned that IPv4 addresses are 32-bit. That means we roughly have 4.3 billions of IPv4 addresses (2^32). But not all of those are publicly available. Some of them are local and some of them are reserved for experimental and multicast purposes. On the past section, we specified class D as multicast ranges and class E as experimental usage. But we didn't specify the local IP ranges.
Local IP Ranges
1. 192.168.0.0 to 192.168.255.255
These IP range might be the most popular local IP range. Your regular routers use this IP range to assign themselves and also assign multiple devices. You might have use this format of IP while connecting to each other in gaming LAN-Parties and such. The first 16 bits are fixed (192.168.0.0/16), so we would have around 64k (2^16) IP addresses in this range. Look at the picture below:
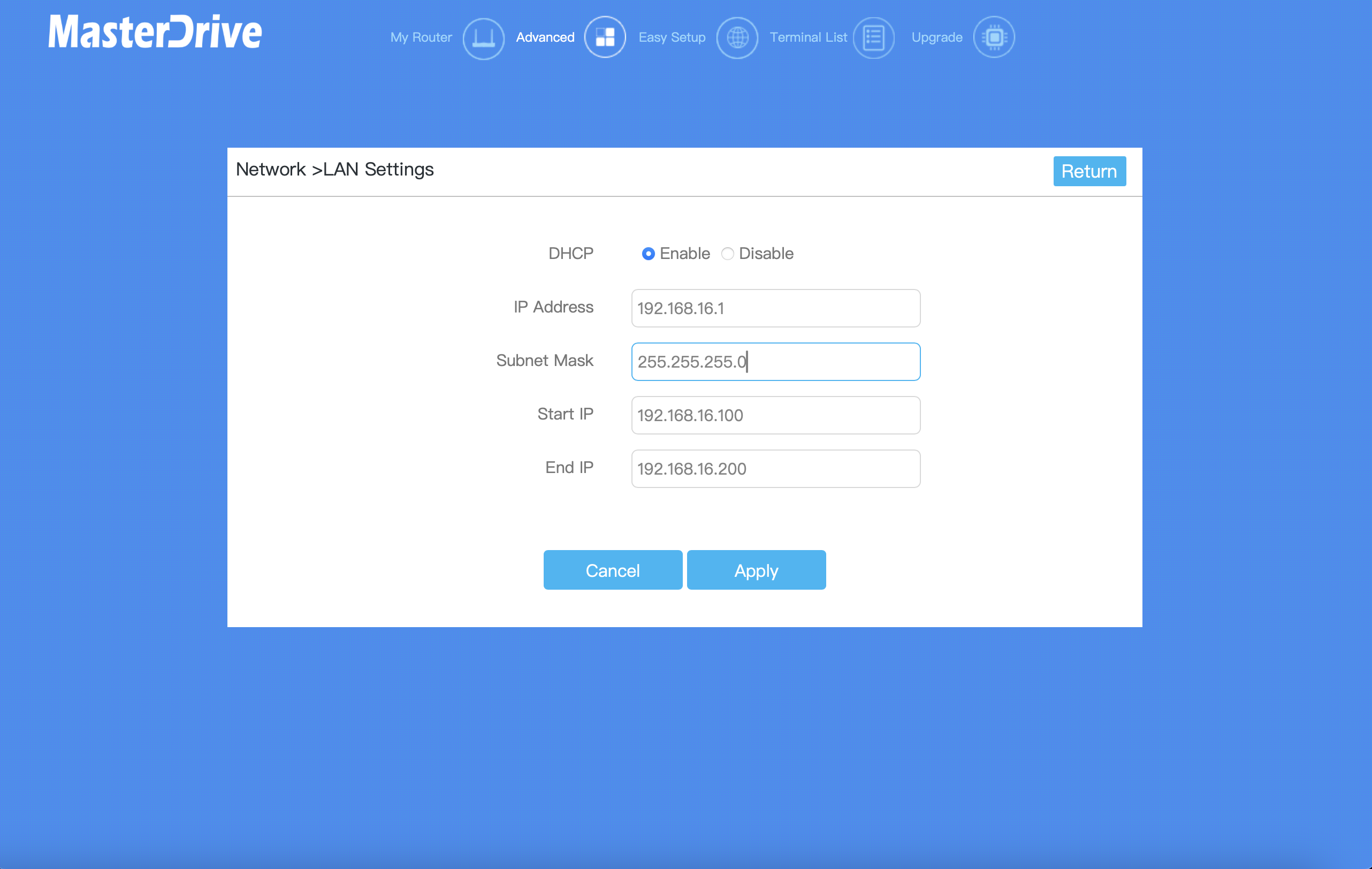 This is an example of a routers LAN (Local Area Network) settings tab on it's panel. The panel's address is usually written on a label on the router. In my case it's 192.168.16.1
This is an example of a routers LAN (Local Area Network) settings tab on it's panel. The panel's address is usually written on a label on the router. In my case it's 192.168.16.1
There are some fields and options here. These fields are default fields and are not modified. here's a break down of each of these:
-
DHCP (Enable/Disable):
- Enable: This option allows the router to automatically assign IP addresses to devices on our network.
- Disable: If disabled, we'll need to manually assign IP addresses to each device on our network.
-
IP Address:
- This is the IP address of the router itself on the local network. It is typically used as the gateway for all devices connected to the router. In our case, it is set to "192.168.16.1".
-
Subnet Mask:
- The subnet mask defines the range of IP addresses that are available on the local network. Here, it is set to "255.255.255.0", which means the network can support up to 254 devices (IP addresses from "192.168.16.1" to "192.168.16.254").
-
Start IP:
- This is the starting IP address that the DHCP server will assign to devices on the network. In our case, it is set to "192.168.16.100".
-
End IP:
- This is the ending IP address that the DHCP server will assign to devices on the network. In our case, it is set to "192.168.16.200".
How DHCP works?
Dynamic Host Configuration Protocol (DHCP), works with a particular order which is reffered as DORA. Discover, Offer, Request and Acknowledge.
1. On Discovery, when a client connects to a network (with physical ports or WIFI), it broadcasts a DHCP Discover message to find available DHCP servers. This message is sent to the IP address 255.255.255.255 (broadcast address) because the client doesn't yet have an IP address.
2. Any DHCP server on the network that receives the Discover message responds with a DHCP Offer message. This message contains an available IP address and other network configuration parameters such as the subnet mask, default gateway, and DNS server addresses.
3. The client receives the DHCP Offer messages and chooses one of them. It then sends a DHCP Request message back to the DHCP server that made the offer, indicating its acceptance of the proposed IP address and configuration.
4. The DHCP server receives the Request message and sends back a DHCP Acknowledgment (ACK) message, confirming that the IP address has been leased to the client for a specific duration (lease time). The client can now use the IP address and the other provided network settings.
Watch this video to have a better underestanding of DHCP:
Now this is a picture of my router and all of the devices connected to it:
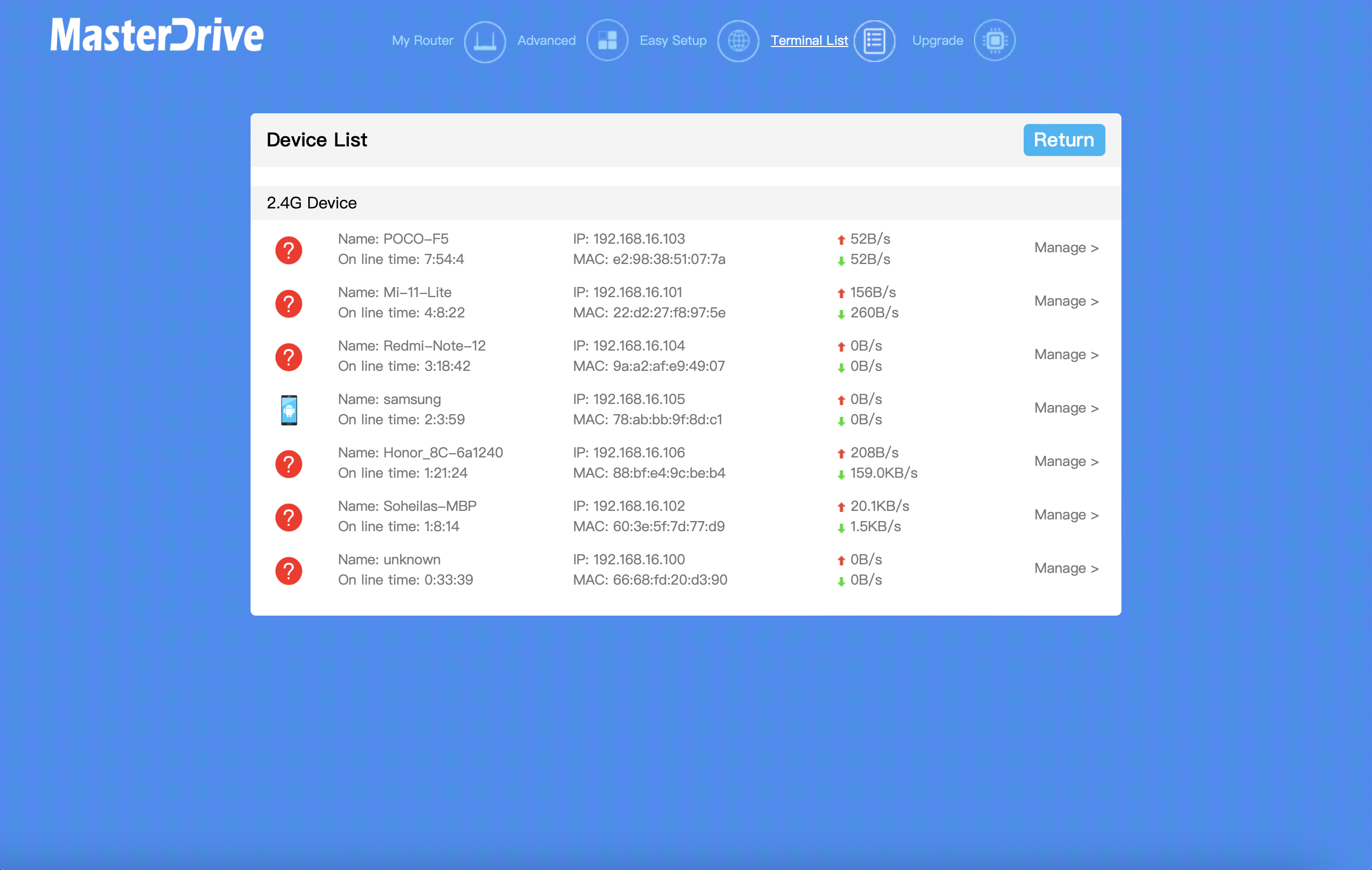 As you can see, the devices have completed the "DORA" steps on DHCP and have their own unique IP addresses.
As you can see, the devices have completed the "DORA" steps on DHCP and have their own unique IP addresses.
Most Internet service providers (ISP), assign a dynamic IP address when their client becomes online. This means that the IP address can change each time you connect to the internet (there is an small probability to get the same IP address). But you can contact your ISP and request an static IP address for a little bit more price. Static IP addresses are permanent and they won't change If you even get offline. Static IPs are crucial for servers and datacenters to ensure that their clients can always find them.
2. 172.16.0.0 to 172.31.255.255
These are also local IP ranges suitable for large and industrial networks. First 12 bits are fixed (172.16.0.0/12). So we would have about 1 million of IP addresses in this particular range (2^20)
3. 10.0.0.0 - 10.255.255.255
These range, since the first 8 bits are fixed (10.0.0.0/8), we would have around 16 millions of IPs (2^24). This is a very large range and It's used by very big corporations, or a whole country.
4. And the last 127.0.0.0 to 127.255.255.255
These range is known for loopback addresses. IPs in this range are not public, not local, but in the very least, private. These IP addresses are mainly for testing and development purposes on the machine itself without needing a physical network.
Modems, Routers Or Modem-routers?
Let's say you have a modem that has fiber or adsl connection on it. You can connect to it via Wifi or physical LAN ports. Modem's that can both be an internet source and do the distribution, are called modem-routers. So they can be both modem and router, which is the case nowadays on consumer-grade modems. But routers are also popular. Routers often expand the range of modems and are used in large buildings and companies to help the internet distribution. Routers can distribute wirelessly (WIFI) or using physical ports. Or both!
In the example pictures of my router, the IP address of my router is 192.168.16.1 and it's connected to my modem-router which has an IP address of 192.168.1.1
If those IP addresses were the same, connection would be established but the communication with modem-router could not be established (We still can use the public internet). For example, we could not use the modem-routers panel in order to configure stuff. we would have to disconnect from the router and connect to he modem-router in order to use modem-routers IP address, or use the modem-routers DNS address. In order to fix this issue, we would have to change the IP address of either one of the 2 devices.
Let's say the modem-router is the main source of our internet. we connect a router to it in order to expand the internet. we connect a second router to our first router in order to expand even more. we connect a third router to our second router and... this goes on and on. Now we have a very expanded and big local network (ignore the IP address limit for now).
World Wide Web (WWW)
Now imagine each of the routers are internet antennas, and the ethernet cables between them are fiber lines. And imagine a lot of them around our globe. Congratulations! we have the modern internet now! with help of the public IP addresses, this has been made possible for humans to create the digital world. Since this is so similar to an spider's web, we are calling it web or net. More connections between each internet stations, the better internet for global use and less ping time between them.

2-4. Transmission Control Protocol (TCP)
Transmission Control Protocol (TCP) is a communications standard that enables application programs and computing devices to exchange messages over a network. It is designed to send packets across the internet and ensure the successful delivery of data and messages over networks.
TCP is one of the basic standards that define the rules of the internet and is included within the standards defined by the Internet Engineering Task Force (IETF). It is one of the most commonly used protocols within digital network communications and ensures end-to-end data delivery.
TCP organizes data so that it can be transmitted between a server and a client. It guarantees the integrity of the data being communicated over a network. Before it transmits data, TCP establishes a connection between a source and its destination, which it ensures remains live until communication begins. It then breaks large amounts of data into smaller packets, while ensuring data integrity is in place throughout the process.
As a result, high-level protocols that need to transmit data all use TCP Protocol. Examples include peer-to-peer sharing methods like File Transfer Protocol (FTP), Secure Shell (SSH), and Telnet. It is also used to send and receive email through Internet Message Access Protocol (IMAP), Post Office Protocol (POP), and Simple Mail Transfer Protocol (SMTP), and for web access through the Hypertext Transfer Protocol (HTTP).
UDP
An alternative to TCP in networking is the User Datagram Protocol (UDP), which is used to establish low-latency connections between applications and decrease transmissions time. TCP can be an expensive network tool as it includes absent or corrupted packets and protects data delivery with controls like acknowledgments, connection startup, and flow control.
UDP does not provide error connection or packet sequencing nor does it signal a destination before it delivers data, which makes it less reliable but less expensive. As such, it is a good option for time-sensitive situations, such as Domain Name System (DNS) lookup, Voice over Internet Protocol (VoIP), and streaming media. Since the rise of modern internet, connections became more stable and fear of having packet loss is now almost zero (when an internet link becomes crowded, it get's bottlenecked and it would cause loss of packets). Which made UDP more popular. Online video games also use UDP in order to achieve the best ping time.
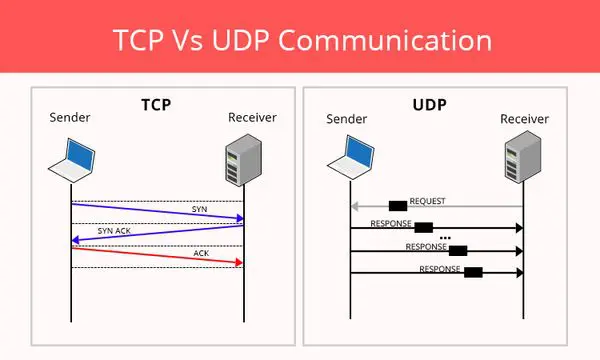
TCP vs IP: What is the difference?
TCP and IP are separate protocols that work together to ensure data is delivered to its intended destination within a network. IP obtains and defines the address—the IP address—of the application or device the data must be sent to. TCP is then responsible for transporting and routing data through the network architecture and ensuring it gets delivered to the destination application or device that IP has defined. Both technologies working together allow communication between devices over long distances, making it possible to transfer data where it needs to go in the most efficient way possible.
In other words, the IP address is akin to a phone number assigned to a smartphone. TCP is the computer networking version of the technology used to make the smartphone ring and enable its user to talk to the person who called them.
Now that we’ve looked at TCP and IP separately, what is TCP/IP? The two protocols are frequently used together and rely on each other for data to have a destination and safely reach it, which is why the process is regularly referred to as TCP/IP. With the right security protocols in place, the combination of the TCP/IP allows users to follow a safe and secure process when they need to move data between two or more devices.
Data packets sent over TCP/IP are not private, which means they can be seen or intercepted. For this reason, it is vital to avoid using public Wi-Fi networks for sending private data and to ensure information is encrypted. One way to encrypt data being shared through TCP/IP is through a virtual private network (VPN). Although encryption gets applied to almost every packet of data. Encryption are out of scope of this tutorial. But let me give you an example. websites that start with "http://" are not encrypted and while you input a password on it (such as 12345678), it can be visible if you are on an insecure network. But the websites that begin with "https://", are encryped using SSL. for example, the same 12345678 password would be encrypted and shown as something like: "o1q0la78)@00!anhc^p2o+5bgzlr)g3p+biz(u&1m!" to the third-party person. Later on, the encrypted data will get decrypted on the origin destination.
2-5. Ports
A port is a virtual point where network connections start and end. Ports are software-based and managed by a computer's operating system. Each port is associated with a specific process or service. Ports allow computers to easily differentiate between different kinds of traffic: emails go to a different port than webpages, for instance, even though both reach a computer over the same Internet connection. Think of it as doors to a house. House being the destination, and the doors being the ports. Multiple people can use multiple doors simultaneously in order to do what they desire.
What is a port number?
Ports are standardized across all network-connected devices, with each port assigned a number. Most ports are reserved for certain protocols — for example, all Hypertext Transfer Protocol (HTTP) messages go to port 80. While IP addresses enable messages to go to and from specific devices, port numbers allow targeting of specific services or applications within those devices.
How do ports make network connections more efficient?
Vastly different types of data flow to and from a computer over the same network connection. The use of ports helps computers understand what to do with the data they receive.
Suppose Bob transfers an MP3 audio recording to Alice using the File Transfer Protocol (FTP). If Alice's computer passed the MP3 file data to Alice's email application, the email application would not know how to interpret it. But because Bob's file transfer uses the port designated for FTP (port 21), Alice's computer is able to receive and store the file.
Meanwhile, Alice's computer can simultaneously load HTTP webpages using port 80, even though both the webpage files and the MP3 sound file flow to Alice's computer over the same WiFi connection.
What are the different port numbers?
There are 65,535 possible port numbers, although not all are in common use. Some of the most commonly used ports, along with their associated networking protocol, are:
- Ports 20 and 21: File Transfer Protocol (FTP). FTP is for transferring files between a client and a server.
- Port 22: Secure Shell (SSH). SSH is one of many tunneling protocols that create secure network connections.
- Port 25: Historically, Simple Mail Transfer Protocol (SMTP). SMTP is used for email.
- Port 53: Domain Name System (DNS). DNS is an essential process for the modern Internet; it matches human-readable domain names to machine-readable IP addresses, enabling users to load websites and applications without memorizing a long list of IP addresses.
- Port 80: Hypertext Transfer Protocol (HTTP). HTTP is the protocol that makes the World Wide Web possible.
- Port 123: Network Time Protocol (NTP). NTP allows computer clocks to sync with each other, a process that is essential for encryption.
- Port 179: Border Gateway Protocol (BGP). BGP is essential for establishing efficient routes between the large networks that make up the Internet (these large networks are called autonomous systems). Autonomous systems use BGP to broadcast which IP addresses they control.
- Port 443: HTTP Secure (HTTPS). HTTPS is the secure and encrypted version of HTTP. All HTTPS web traffic goes to port 443. Network services that use HTTPS for encryption, such as DNS over HTTPS, also connect at this port.
- Port 500: Internet Security Association and Key Management Protocol (ISAKMP), which is part of the process of setting up secure IPsec connections.
- Port 587: Modern, secure SMTP that uses encryption.
- Port 3389: Remote Desktop Protocol (RDP). RDP enables users to remotely connect to their desktop computers from another device.
2-6. Domain Names
A domain name is a string of text that maps to an alphanumeric IP address, used to access a website from client software. In plain English, a domain name is the text that a user types into a browser window to reach a particular website. For instance, the domain name for Google is ‘google.com’.
The actual address of a website is a complex numerical IP address (e.g. 192.0.2.2), but thanks to DNS, users are able to enter human-friendly domain names and be routed to the websites they are looking for. This process is known as a DNS lookup.
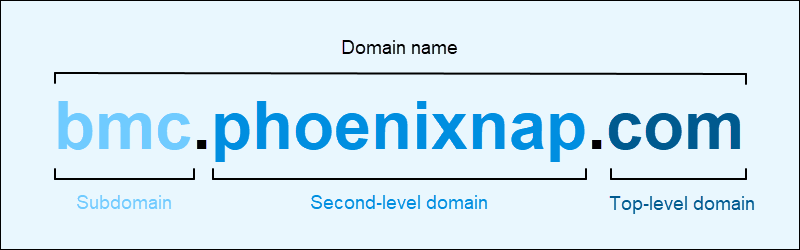
2-7. Domain Name System (DNS)
The Domain Name System (DNS) is the phonebook of the Internet. Humans access information online through domain names, like nytimes.com or espn.com. Web browsers interact through Internet Protocol (IP) addresses. DNS translates domain names to IP addresses so browsers can load Internet resources.
Each device connected to the Internet has a unique IP address which other machines use to find the device. DNS servers eliminate the need for humans to memorize IP addresses such as 192.168.1.1 (in IPv4), or more complex newer alphanumeric IP addresses such as 2400:cb00:2048:1::c629:d7a2 (in IPv6).

How does DNS work?
The process of DNS resolution involves converting a hostname (such as www.example.com) into a computer-friendly IP address (such as 192.168.1.1). An IP address is given to each device on the Internet, and that address is necessary to find the appropriate Internet device - like a street address is used to find a particular home. When a user wants to load a webpage, a translation must occur between what a user types into their web browser (example.com) and the machine-friendly address necessary to locate the example.com webpage.
In order to understand the process behind the DNS resolution, it’s important to learn about the different hardware components a DNS query must pass between. For the web browser, the DNS lookup occurs "behind the scenes" and requires no interaction from the user’s computer apart from the initial request.
Some Of The Popular Free And Public DNS Servers
| Provider | Primary DNS | Secondary DNS |
| 8.8.8.8 | 8.8.4.4 | |
| Control D | 76.76.2.0 | 76.76.10.0 |
| Quad9 | 9.9.9.9 | 149.112.112.112 |
| OpenDNS Home | 208.67.222.222 | 208.67.220.220 |
| Cloudflare | 1.1.1.1 | 1.0.0.1 |
| AdGuard DNS | 94.140.14.14 | 94.140.15.15 |
| CleanBrowsing | 185.228.168.9 | 185.228.169.9 |
| Alternate DNS | 76.76.19.19 | 76.223.122.150 |
You can set DNS server on Windows from control panel > network & internet > network and sharing center > change adapter settings > double click on your network adapter > properties > internet protocol version 4 (TCP/IPv4) > use the following DNS server addresses > input your dns server, hit ok until all the windows gets closed and you have now set a DNS server!
On linux, edit "/etc/resolv.conf" file with sudo privileges and add your DNS servers.
A bad DNS server can slow down IP resolving and overall make your internet feel slow. On the other hand, good DNS servers can improve it. We all know the Cloudflare (1.1.1.1) is the GOAT!
2-8. Playing With DNS
Since DNS acts as a phonebook of the internet, we can have our own phonebook! On Windows operating systems, there is a "hosts" file in the corresponding path: "C:\Windows\System32\drivers\etc". Run a notepad (or any editors) as an administrator and open the path. In that folder, open the "hosts" file. On Linux based operating systems, the file is placed in "/etc/hosts" path. You should edit it with sudo privileges. Now, you can set any desired domain name to a corressponding IP. If you have any servers on cloud, you can try your servers IP. But for now, you can practice on your routers gateway IP. In most cases, the routers IP is "192.168.1.1". Set any domains you what to that IP address. Since this is happening locally and it's just a fun thing, the domain can be anything, even a single word. For this, I wanna set "my.router" as the domain name for my router's panel. My routers IP address is 192.168.27.1 So I'm gonna set that. I'm adding the line below to the hosts file:
192.168.27.1 my.router
Now I have set "my.router" domain address to my routers IP address. If I save the hosts file, I can visit my routers panel using the "my.router" domain. http://my.router. If you've done this steps exactly like me with the correct router IP address, then the link would work for you. But since this is just happening locally on your PC, other people won't be able to use your custom domain.
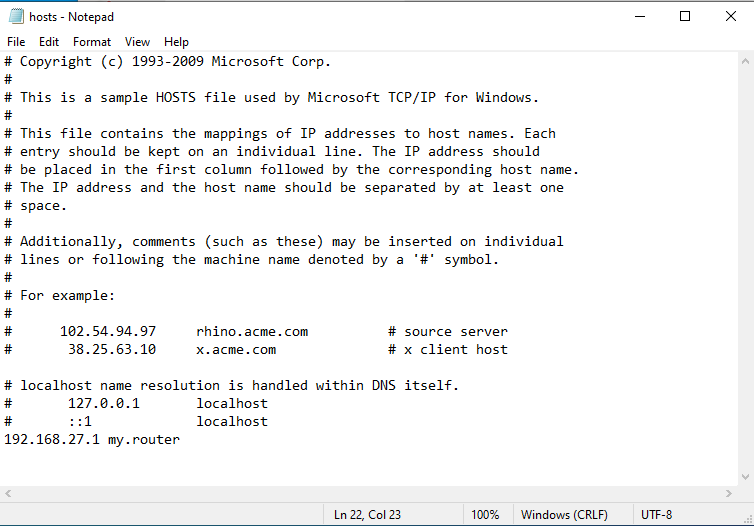
example of the hosts file and applied domain on windows
You can also get the IP address from a domain name. open a command prompt on Windows or a Terminal on Linux. and just type write the "ping" command and write in your desired domain name. For example, let's get the IP address of this website:
ping rootamin.ir
After hitting enter on your keyboard, the console will start pinging the website and returning an IP address.
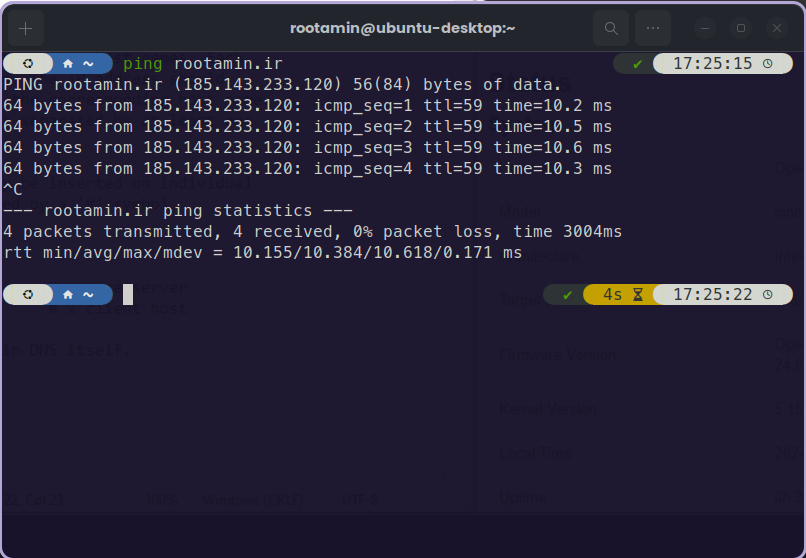 example of pinging a website on Ubuntu linux terminal
example of pinging a website on Ubuntu linux terminal
As you can see in the picture, the console returned an IP address of a server. For big websites such as Google, this IP addresses can be different by the location where the pinging happens. This is because Google has to distribute it's traffic through multiple servers in order to keep itself fast and stable. You can use websites such as https://check-host.net in order to see multiple IP addresses in multiple locations.
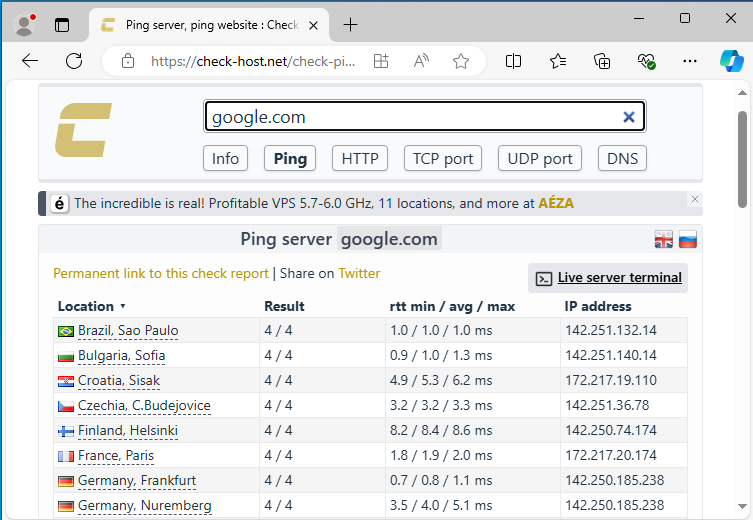 example of pinging google.com on check-host website in order to see multiple IP addresses in multiple locations.
example of pinging google.com on check-host website in order to see multiple IP addresses in multiple locations.
Sources:
https://en.wikipedia.org/wiki/Computer_network
https://x.com/SecurityTrybe/status/1806475086947352984
https://www.fortinet.com/resources/cyberglossary/tcp-ip
https://cyberhoot.com/cybrary/transmission-control-protocol-tcp/
https://www.cloudflare.com/learning/network-layer/what-is-a-computer-port/
https://www.cloudflare.com/learning/dns/glossary/what-is-a-domain-name/
https://www.cloudflare.com/learning/dns/what-is-dns/
https://www.lifewire.com/free-and-public-dns-servers-2626062
Gathered, written and modified by rootamin
ups!
╞ Reply